Phishing: what it is and how to avoid becoming a victim of fraud
Kyiv • UNN
An overview of common phishing methods and tips on how to protect yourself from online fraudsters. Experts advise to be vigilant, check information, and avoid clicking on suspicious links.

Your personal data in the global network is a tasty morsel for fraudsters. UNN has gathered information for you about what phishing is - one of the most common methods of fraudsters' actions - and how to avoid falling into the trap.
Catch a fish
"Phishing" refers to an attempt to steal sensitive information, usually in the form of usernames, passwords, credit card numbers, bank account information, or other sensitive data, in order to use or sell the stolen information. By masquerading as a reputable source with an attractive request, the attacker lures the victim to deceive them, much like a fisherman uses bait to catch a fish," is how the term is defined by experts from Cloudflare, an American company that works in the field of data protection.
Experts divide phishing attacks into several types:
- Prepaid fraud is a well-known scheme, often also referred to as “Nigerian Prince”. Fraudsters try to gain the victim's trust by swindling them out of a relatively small amount of money, promising to transfer a much larger sum later. Usually, the scammers tell a story about a wealthy person who is in a difficult situation or can use a story about an inheritance from a distant relative from another country. The first cases of such fraud appeared long before the Internet - in the 19th century. Back then, it was known as the “Spanish prisoner scam” - fraudsters posed as people who were allegedly trying to rescue and transport a wealthy Spanish prisoner who was willing to pay a generous reward for helping to bribe prison guards. The easiest and most effective way to avoid such an attack is simply not to respond to it. If something seems too good to be true, it usually is.
- Account deactivation scams are a more sophisticated way to get the victim to hand over their personal data to avoid deactivation of an allegedly important account. In such cases, fraudsters pretend to be employees of banks or other financial institutions and send messages about the need to confirm their data to avoid deactivation/blocking of the account or account. In such cases, you should not rush - it is better to go directly to the website of the service or institution from which you allegedly received the message, review the information regarding possible requests from them and/or contact the support service. It is important that you should not go to the company's website directly from the message, but separately.
- Website fraud - this method is usually combined with the previous one. In this case, fraudsters create a fake website that is almost identical to the legitimate website of the company whose services the victim uses. You can come across such a site by clicking on a message, a link on a forum, or even a search engine. All information that the victim enters on such a site is collected for sale or other criminal use. You should carefully check the URL (website address), if it is questionable, looks different from the usual, you should not enter the data. Suspicion should also be raised by sites that the browser marks as unsafe, which do not have the HTTPS protocol - even if it is a legitimate company website, it is likely to have been attacked.

"Phishing can be targeted, i.e., directed at specific individuals or companies. Currently, this is one of the most common types of phishing and the most effective.
Sometimes fraudsters use cloning techniques, for example, imitating a legitimate email previously received by the victim, while replacing secure links with fraudulent ones. Also, scammers can disguise their messages as content that will definitely require the attention of a potential victim, such as messages from management, bills. This type of phishing is sometimes called "whaling."
Ukrainian realities
In Ukraine, one of the most common types of phishing is fraud on trading platforms. According to the National Bank of Ukraine, fraudsters can impersonate buyers. An example of such a situation is when a pseudo-buyer informs the seller that he or she has made a purchase via OLX Delivery and that in order to receive funds, the seller needs to follow an individual link and provide his or her card details.
After the seller clicks on the link and enters all the card details, the fraudster asks the seller for the card balance and the SMS code from the bank. After receiving the information, the fraudster appropriates funds from the accounts.
In order to mislead sellers, fraudsters also create fraudulent websites that visually resemble the websites of marketplaces (e.g. OLX). Such fake pages may also have a form of chat that has nothing to do with real OLX support.
To avoid such fraud and sell online safely, experts from the #CybersecurityFinance project advise:
- discuss the details of the transaction exclusively in the chat of the trading platform or using the platform's application, as fraudsters can send phishing links to third-party messengers (Viber, Telegram, WhatsApp). Remember, you can only provide a 16-digit card number, which is enough information to receive payment for the goods;
- do not click on links from strangers. Check the address first, and only then follow the link.
- to check the addresses of websites where you enter payment card details, logins and passwords to online banking.

Another type of fraudulent scheme is "Fake polls and voting". Fraudsters conduct fake polls and votes for which you can allegedly receive a reward, for example, in the amount of 500 hryvnias. The topic of such polls and votes can be different, for example, to cast your vote on a website where voting for a certain brand of cosmetics is taking place, and fraudsters indicate a well-known brand to be convincing.
In order to vote, you need to follow the instructions, where one of the prerequisites is the need to be authorized and enter the login and password to your own social media page. When a person enters these data, they become automatically known to fraudsters who gain access to the page.

Once the page is accessed, fraudsters can:
- post similar offers on social media on behalf of the account owner to gain access to the pages of the page owner's followers;
- asking for loans and financial assistance from the page's followers. There are cases when fraudsters use photos of relatives and friends published on the owner's page and write that someone close to them has been in an accident and urgently needs money. To be more convincing, fraudsters may attach screenshots of medical reports and various medical certificates with stamps, which may look quite believable.
How to protect yourself from fraudsters?
- Don't trust offers that say you can get money in a few clicks. Easy money is usually offered by fraudsters.
- Check information on official websites if it is a well-known brand.
- Do not click on links from strangers and be careful about links sent by your friends. Remember, fraudsters could have hacked your friend's page.
Another scheme is "Message on behalf of Meta".
Fraudsters on behalf of Meta write to personal messages (Direct) on Facebook and Instagram and lure passwords to social media pages. Messages may be sent in English. The content of the message is that allegedly Meta employees are informing the page owner that the community rules have been violated. The scammers may also write that after reviewing your page, it was determined that you have infringed copyright several times. If you think this is a mistake, you should dispute it, otherwise your account will be deactivated within 24 hours. And they provide a link to the appeal form, while when the page owner clicks on the link, the fraudulent resource asks for their own social media login and password. Once a person enters this data, it automatically becomes known to the fraudsters.
Remember, Instagram and Facebook never write about account security in Direct messages. Emails from Meta (Instagram and Facebook) regarding your account security and login that were sent within the last 14 days can be found in the Security section.
Fraudulent scheme "Please sign the petition."
Fraudsters are spreading requests to sign a petition to award the title of Hero of Ukraine posthumously by distributing phishing links. To do this, they can send such requests in personal messages in messengers and make relevant posts on social media.
The fraudsters' requests look convincing, as they create a plausible text of the petition, visual design, indicate the name, surname, patronymic of the military and may indicate the real number of the petition, etc.
What is the goal of fraudsters?
In this way, scammers try to find out the login and password to social media pages in order to gain access to them in the future. After all, when a person clicks on a fraudulent link to sign a petition, the fraudulent service asks for login information to the social media page, allegedly for authorization.
How to avoid fraud?
Don't click on links from strangers, even if they ask you to sign a petition. The link to the petition should look like this: https://petition.president.gov.ua/petition/ (+ petition number), all other links are fraudulent and should not be clicked on.
If you receive such a request from a friend on social media, help them, but be careful. Do not follow links even from friends, as fraudsters can hack social media pages and post on their behalf. To sign the petition, find it on the official website
President of Ukraine: https://petition.president.gov.ua/ by its number. You can also enter the Hero's surname, name and patronymic in a Google search and go to the official website.
To sign a petition, you must actually log in, but never through social media. To sign a genuine petition, you must confirm your identity using an electronic signature or BankID.
To protect your own social media pages:
- set up multi-factor authentication. This function is available in your account settings and may be called two-step verification, which means that to log in to your account, in addition to your login and password, you need to enter a verification code sent to your smartphone, email or the corresponding application;
- do not enter your logins and passwords to accounts on unfamiliar and suspicious websites;
- Create complex and unique passwords for each account.
Fraudulent scheme "Making a cash payment".
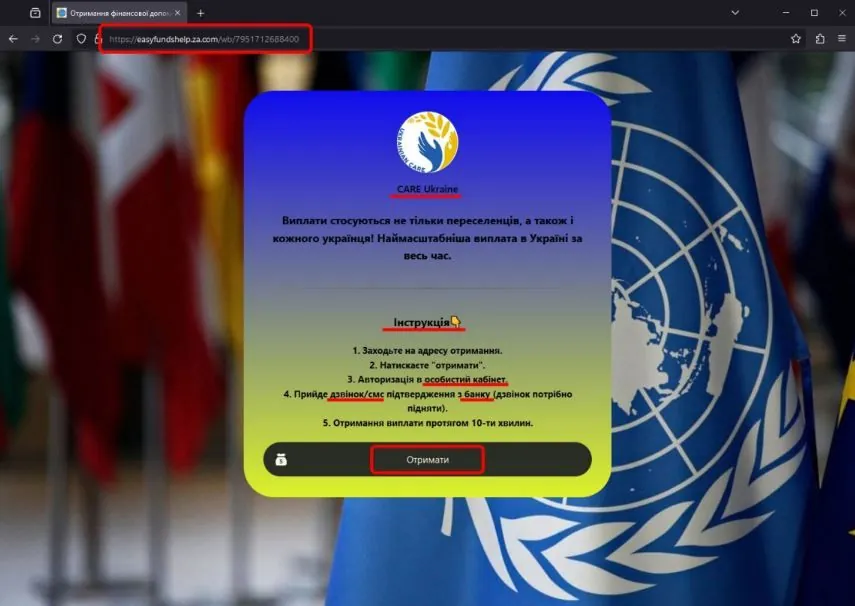
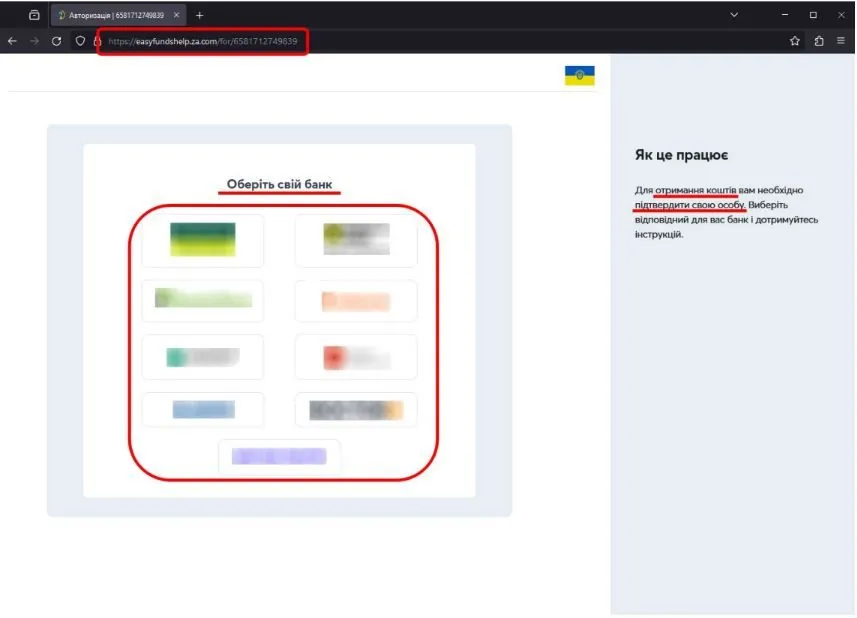
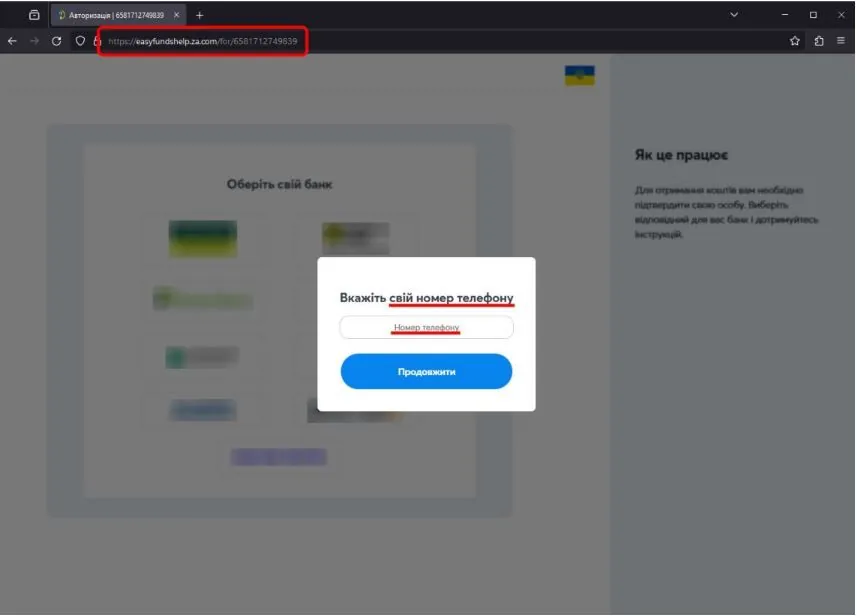
Through social networks and messengers, fraudsters spread messages about the possibility of receiving a cash payment for every Ukrainian. The message contains an active link to a phishing page, which can be stylized using the identity of a charitable and/or international government organization. On this page, fraudsters post instructions on how to complete the identification process, as well as active links to fraudulent phishing resources that are disguised as bank authorization pages.
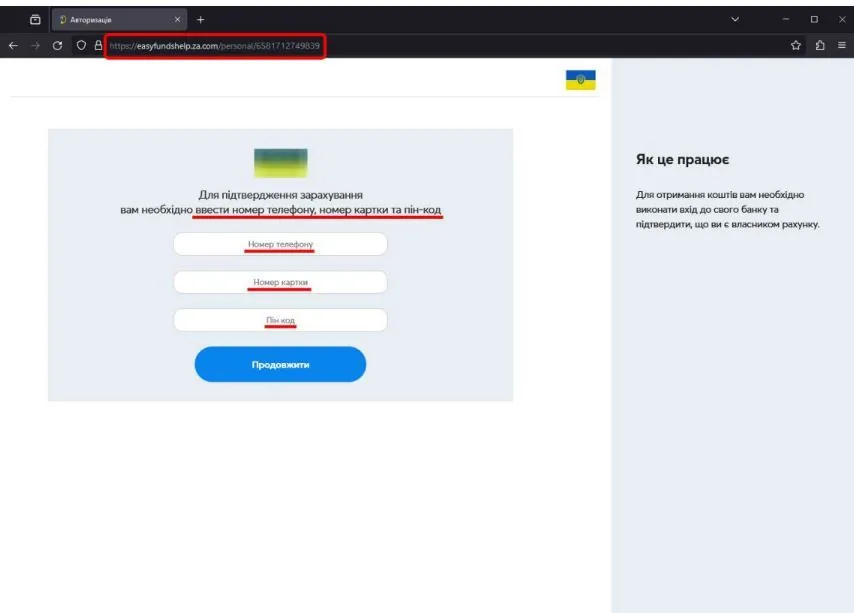
To make a cash payment, the fraudulent resource offers to enter a mobile phone number, password to the personal account, payment card number, CVV, pin code, and current card balance to confirm the login to the personal account. The fraudsters use this information to "link" the user's account to a new device or for online authorization on the portal of the relevant bank, which allows them to withdraw funds from the victim's account.
Such fraud schemes are very common.
- Check any information about cash payments that you see on the Internet or in messages from official sources.
- Do not click on the link provided in such messages. Go to the official website of the respective organization on whose behalf the financial assistance is offered via a search engine by entering the name of the required website.
Below is an image of the fraudulent resource.